Security and information protection is the core of all computer networks and communication systems. The convergence of fixed-mobile and voice-data networks has opened the door for the innovative and fancy next generation services and applications like integrated multimedia services, combining web browsing, email, instant messaging, presence, VoIP, video conferencing, application sharing, telephony, unified messaging, multimedia content delivery, etc. on top of different network technologies including IPv6, 3GPP (Third Generation Partnership Project) IMS (IP Multimedia Subsystem), 3GPP2 Multimedia Domain (MMD), TISPAN (Telecoms & Internet converged Services & Protocols for Advanced Networks) NGN (Next Generation Network), UMTS (Universal Mobile Telecommunication Systems) and DSL (Digital Subscriber Line) etc. In the context of converged communication world, network security is a big challenge to protect multidimensional and hybrid technology networks resources and to provide confidentiality and integrity protection to users.
The introduction of IP in telecommunication domain signifies not only a shift towards packet switching communication, but also a step towards completely open and easily accessible protocols. In terms of security, this implies an array of new threats and risks that have to be counter. The IMS is vulnerable to different types of other attacks because users are always being connected, online and the network structure based on new SIP (Session Initiation Protocol) [5] technology which is open architecture and vulnerable to different types of Denial-of-Service (DoS)/Distributed Denial-of-Service (DDoS) attacks.
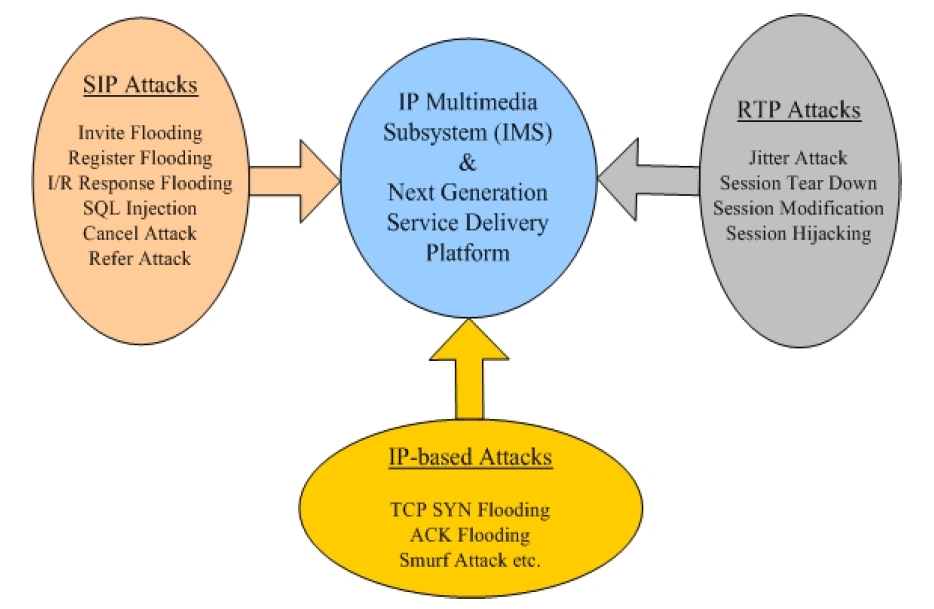
The IMS potential threats are from multiple communication domains and protocols including Session Initiation Protocol (SIP), Media Streaming (RTP) and Internet (IP) as depicted in figure above. These security challenges are summarized as follows:
• Denial-of-Service (DoS) attacks on IMS Core and NGN Services.
• Distributed Denial-of-Service (DDoS) attacks on IMS.
• Misuses of IMS Services and Applications.
• Threats from open-based IP infrastructure.
• SIP signalling attacks like REGISTER and INVITE flooding.
• Media flow attacks like drop and modify session.
• Vulnerability threats on access links.
In order to minimize the risk of theft of information and data form hackers and protection of network and services, there is strapping requirement to develop an independent security framework for IP Multimedia Subsystem (IMS).